
Big Idea 5.6 Safe Computing

Personal Identifiable Information (PII)
Personal Identifiable Information or PII is a type of information that is specific to you. For example, your age or race would be an example but something like your favorite cat isn’t (Will insists your diet is a PII but it’s not).
There are times when we want to post our PII online. For example, you would want to upload it to your job profile or a site like LinkedIn because you want people to see it. However, be careful where you upload this data. It will be known by everyone since it’s public.
Some things that you should be cautious about to upload (gray area) would be:
- Birth date
- Place of birth
- Address
- Phone number
- Maiden names
- Drivers License Number
There are things, however, that you will most likely have to upload publicly OR can be found with a quick search. For example:
- Name
- Date of Birth
- SSN
- Bank Account info
- Picture
- What high school you attended
- What college you went to
- Properties you own
- State/City of residence
- Previous residence
You could upload this online (some you have to. Ex: home address for Amazon) but be careful where you upload it. You don’t want to post your mother’s maiden name on social media.
Things that you should keep confidential would be:
- Private credentials for accounts and what-not
- Two-factor authentication
- This is common for sensitive things like financial data
- Social security numbers
- Tax records
- Medical information
- Financial data
Most if not all financial and government documents should be kept private. However, there will be times when you need to share this. For example, if you are applying for a RealID (form of identification), you will need to submit your social security number.
POPCORN HACK 1:
How do you decide what personal information to share online and what to keep confidential?
- Think about why a company would want the information they’re requesting for.
Beware, Establish practices for your own Safety
Authentication
Authentication measures protect devices and information from unauthorized access.
Strong Passwords
The easier the password is to guess, the easier it is to make a mess. Strong passwords:
- 10 or more characters
- Must contain a symbol
- Must contain a number
- Must contain lowercase and uppercase letters
- Avoid dictionary words/things known about you (ex. “Password”, “123456”, your birthday, your name, your pet’s name, etc.) The above are things hackers can look for while guessing your password
Types of Authentication
- What the user knows (ex. passwords, answers to security questions, etc.)
- What you are (ex. biometric data like eye scan, palm print, thumbprint, etc.)
- What you have (ex. keycards, etc.)
Multi-factor Authentication
When one or more of these authentication measures are used, it is considered multi-factor authentication.
Precautions
- Run Virus scans to help prevent malicious code from getting into and affecting your system.
- Keeping the operating system and other software up to date can also fix errors that would allow a virus or malware to compromise a system.
POPCORN HACK 2:
How can multi-factor authentication enhance security?
- Multi-factor authentication can enhance security by increasing the number of steps it takes for an attacker to log in through your account. If someone gets your password and email, they wouldn’t be able to log in unless they have your phone and phone password as well for the second authentication level.
Nefarious Uses of Internet
Virus and Malware
Virus
- Viruses can allow unauthorized access by modifying the operating system to accept any user without authentication.
- Virus malicious programs that can copy themselves and gain access to systems that they are not supposed to be in.
Malware
- Malware is often intended to damage a computing system or take partial control over its operation.
- Infiltrates a system by posing as legitimate programs or by attaching itself to legitimate programs, like an email attachment.
- Malware is often sent in attachments to things in email. Often they request you to click on an attachment and it starts the process of adding a virus to your computer.
Phishing: Phishing is an attempt to trick a user into providing personal information (PII) by using social manipulation. Phishing emails look like they’re from a trusted source. They may appear to be an email from a bank or credit card company or a store. They could also be from a Nigerian prince or a fish who is phishing.
They try to trick you into clicking a link and may try to scare you or lure you with the promise of something like money. The link could cause unexpected harm. They may install a virus or keylogger on your computer. A keylogger records keystrokes made by the user which can be used to get credentials. They could also turn your computer into a rogue access point or a fake wireless network which can be used to infect other computers.
Factors to Increase Security of System
Encryption is a good way to increase security of a system.
- Passwords vs. keys: A password is something used to login or unlock an account, while a key is used to encrypt/decrypt the data being used or transferred by that account.
Demoing cryptography - Symmetric Encryption - Basic ciphers or codes
- Symmetric encryption uses one key to encrypt and decrypt
- Examples: Caesar Cipher, Morse Code, Rail Fence Cipher, PSK, etc.
- Asymmetric encryption is much more secure. It uses public keys to encrypt and private keys to decrypt.
- Examples: RSA, Diffie-Hellman, Public Key Encryption
“Alice and Bob”
Alice wants to send an encrypted message to her friend Bob.
With symmetric key encryption, the following process ensues:

Pretty simple, right! You know what else is simple? Trying to share the encryption/decryption key without letting anyone else know. Enter: Asymmetric Encryption
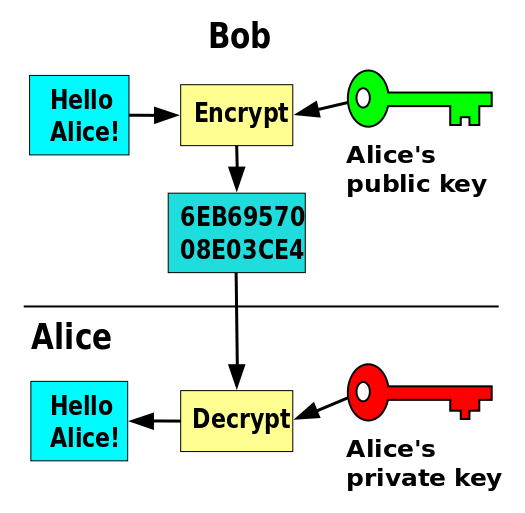
POPCORN HACK 3:
What are the key differences between symmetric and asymmetric encryption?
- Symmetric encryption uses a single shared key for both encryption and decryption, while asymmetric encryption employs a pair of public and private keys, enhancing security by separating these functions and facilitating secure communication over untrusted networks.
SSL/TLS
Uses a Certificate Authority(CA) to generate a signed certificate that proves the server’s legitamacy.

Authentication: SSL/TLS certificates ensure the identity of the server and sometimes the client. They contain information about the entity they are issued to, including the domain name and public key.
Encryption: SSL/TLS certificates facilitate encrypted communication between the client and server. They enable the encryption of data transmitted over the internet, preventing eavesdropping and unauthorized access.
Certificate Authorities (CAs): CAs issue SSL/TLS certificates after verifying the identity of the certificate requester. They act as trusted third parties that sign and validate the authenticity of certificates.
Public and Private Keys: SSL/TLS certificates use asymmetric encryption, involving a public key to encrypt data and a private key to decrypt it. The public key is embedded in the certificate while the corresponding private key is securely held by the server.
Handshake Protocol: When a client connects to a server, they engage in a handshake protocol to establish a secure connection. This involves agreeing on encryption algorithms, exchanging keys, and verifying the authenticity of the certificates.
Expiration and Renewal: SSL/TLS certificates have a validity period. They need to be periodically renewed to maintain secure communication. Expired certificates can disrupt services and pose security risks.
HTTPS: SSL/TLS certificates are commonly used in web browsers to enable HTTPS connections. They signal a secure connection, ensuring data integrity, confidentiality, and authenticity between the web server and the user’s browser.
- Ex: When we used certbot to make our backend server run using HTTPS in the passion project
Firewall and antivirus Firewall and antivirus software is a really good and easy way to protect your computer. Pretty much all computers come with this software and are enabled as a default. Just make sure to not disable it!
![]()
Homework
- Describe PII you have seen on a project in CompSci Principles.
- Names and pictures of ourselves we put on our websites.
- Describe good and bad passwords? What is another step that is used to assist in authentication?
- A good password is at least 15 characters with a good mix of cases, numbers, and special symbols. Another step that can be used to assist in authentication is a phone or device push-notification that serves as a second factor of authentication.
- Try to describe Symmetric and Asymmetric encryption.
- Symmetric encryption works by encrypting a single key with a shared piece of information and decrypting it on the other side to verify authentication. Asymmetric encryption utilizes both public and private keys to develop a key to encrypt information and verify that the authentication is valid.
- Provide an example of encryption we used in AWS deployment.
- We used TLS certificate encryption to ensure data integrity of our website and the connections between our website and the client.
- Create a python script that lets the user input a password that is checked by the program
BONUS: Use online wordlists to compare the password, preventing dictionary attacks
# Code Here for Q5
import requests
def is_strong_password():
password = input("Enter your password: ")
wordlist_url = "https://www.mit.edu/~ecprice/wordlist.10000"
response = requests.get(wordlist_url)
if response.status_code == 200:
wordlist = set(response.text.lower().split())
if len(password) >= 12:
return True
else:
print("Failed to fetch the wordlist. Please check the URL.")
return False
def main():
if is_strong_password():
print("Password is strong. Congrats")
else:
print("Weak password. Choose again buddy")
main()
if __name__ == "__main__":
main()
Defaulting to user installation because normal site-packages is not writeable
Requirement already satisfied: requests in /home/dudeamabobby/.local/lib/python3.10/site-packages (2.31.0)
Requirement already satisfied: urllib3<3,>=1.21.1 in /home/dudeamabobby/.local/lib/python3.10/site-packages (from requests) (2.1.0)
Requirement already satisfied: certifi>=2017.4.17 in /home/dudeamabobby/.local/lib/python3.10/site-packages (from requests) (2023.11.17)
Requirement already satisfied: charset-normalizer<4,>=2 in /home/dudeamabobby/.local/lib/python3.10/site-packages (from requests) (3.3.2)
Requirement already satisfied: idna<4,>=2.5 in /home/dudeamabobby/.local/lib/python3.10/site-packages (from requests) (3.6)
Password is strong. Congrats